Cyber weapons of mass destruction
The modern world has been digitized. Not yet fully, but its "digitalization" is developing at a rapid pace. Almost everything is already connected to the network or will be connected in the near future: financial services, utilities, industrial enterprises, the armed forces. Almost everyone has a smartphone in use, “smart homes” are gaining popularity - with smart TVs, refrigerators, vacuum cleaners, washing machines, microwave ovens and even light bulbs.
The first car has already appeared - the Honda Legend, with an installed third-level autopilot, which fully controls the car up to the possibility of emergency braking. The “driver” is only required to be ready to take control for a certain time specified by the manufacturer (on Tesla electric vehicles, the second level autopilot is installed, which requires constant monitoring by the driver).

In the near future, the autopilot will be able to completely replace the driver behind the wheel of a car.
Many companies are working to create a human-computer interface that will directly connect the brain to external devices. One such company is Neuralink of the ubiquitous Elon Musk. It is expected that such devices will make life easier for people with disabilities, but there is no doubt that these technologies will find application in other areas. In the future - in totalitarian countries, where phobias about "chipping" may well become a reality.
But while digital systems and services make life incredibly easier for people, increase the efficiency of industrial and municipal facilities. Everything seems to be fine, but there is one "but". All digital systems are theoretically hackable. And from time to time this is confirmed by practice.
Computer viruses
The theoretical foundations for the development of "computer viruses" were formulated almost simultaneously with the appearance of computers themselves in the middle of the 1961th century by John von Neumann. In XNUMX, Bell Telephone Laboratories engineers Viktor Vysotsky, Doug McIlroy, and Robert Morris developed programs that could make copies of themselves. These were the first viruses. They were created in the form of a game that the engineers called "Darwin", the purpose of which was to send these programs to friends to see which one destroyed more of the opponent's programs and made more copies of its own. The player who managed to fill the computers of others was declared the winner.
In 1981, the Virus 1,2,3 and Elk Cloner viruses appeared for the Apple II personal computer (PC), which any owner of these PCs could "get acquainted" with. A few years later, the first anti-virus programs appeared.

Apple II became the first consumer computer for which computer viruses were created
The word combination "computer virus", which has become firmly established in everyday life, essentially hides many types of malicious software: worms, rootkits, spyware, zombies, adware ), blocking viruses (winlock), Trojan viruses (trojan) and their combinations. In what follows, we will also use the term "computer virus" as a general term for all types of malware.
If the first viruses were most often written for entertainment, pranking, or as an indicator of the programmer's abilities, then over time they began to "commercialize" more and more - to steal personal and financial data, disrupt equipment, encrypt data for extortion, display intrusive ads, and so on. ... With the advent of cryptocurrencies, computer viruses received new functionality - they began to take users' computers "into slavery" for mining (extracting) cryptocurrencies, forming huge networks of infected PCs - botnets (before that, botnets also existed, for example, to carry out "spam" mailings or the so-called DDoS attacks).
Such opportunities could not fail to interest the military and special services, which, in general, have similar tasks - to steal something, to break something ...
Cyber Troops
Given the importance and openness of digital infrastructure, states are aware of the need to protect it, for the purpose of which, within the framework of the ministries of defense and special services, appropriate units are created, designed both to protect against cyber threats and to carry out attacks on the enemy's digital infrastructure.
The latter is usually not advertised, however, the now former US President Donald Trump has officially expanded the powers of the US Cyber Command (USCYBERCOM, US Cyber Command), allowing them to carry out a preemptive attack on potential opponents (and possibly on allies - you must somehow help your economy?). The new powers allow military hackers to carry out subversive activities in the networks of other states "on the brink of hostilities" - to carry out espionage in computer networks, sabotage and sabotage in the form of the spread of viruses and other special programs.
In 2014, by decree of the President of the Russian Federation V.V.Putin, the Information Operations Troops were formed, and in January 2020, it was announced that special units were created in the Russian Armed Forces to conduct information operations, as announced by the Minister of Defense of the Russian Federation Sergei Shoigu.
There are cybernetic troops in other developed countries as well. According to unconfirmed reports, the budget of the US cyber troops is about $ 7 billion, and the number of personnel exceeds 9000 people. The number of Chinese cyber troops is about 20 people with funding of about $ 000 billion. Britain and South Korea are spending $ 1,5 million and $ 450 million on cybersecurity, respectively. Russian cyber troops are believed to include about 400 people, and the costs are about $ 1000 million.
Goals and opportunities
The potential destructiveness of computer viruses is enormous, and they are rapidly increasing as the world around them digitalizes.
Everyone remembers the US accusations against Russia of meddling in the American elections, as well as accusations against China of stealing intellectual property. But manipulation of public conscience and data theft is just the tip of the iceberg. Things get much more serious when it comes to infrastructure vulnerabilities.
Numerous books and films on this topic vividly depict the collapse of infrastructure - the shutdown of utilities, congestion from cars, loss of funds from the accounts of citizens. In practice, this has not happened yet, but this is hardly a consequence of the impossibility of implementation - in articles on cybersecurity on thematic resources, you can find a lot of information about the vulnerability of computer networks, including in Russia (in Russia, perhaps, even to a greater extent for the traditional hope for "maybe").
Most likely, the fact that there have not yet been large-scale infrastructure hacks is a consequence of the lack of interest of serious hacker groups in this topic - their attacks usually have a clear ultimate goal, which is to maximize financial profit. In this regard, it is much more profitable to steal and sell industrial and commercial secrets, compromising evidence, encrypt data, demanding a ransom for their decryption, and the like, than to disrupt the operation of city sewers, traffic lights and power grids.

The collapse of urban infrastructure can be caused not only by cruise missile attacks on data centers and power plants, but also by malicious software.
At the same time, with a high probability, an attack on infrastructure is considered by the military of different countries as an element of warfare, which can significantly weaken the enemy's economy and cause discontent among the population.
In 2010, the private company Bipartisan Policy Center conducted a simulation of a massive cyber attack on the territory of the United States, which showed that during a prepared and coordinated cyber attack, up to half of the country's energy system could be disabled in half an hour, and mobile and wire communications would be disconnected within an hour. , as a result of which financial transactions on the exchange will also stop.
However, an attack on civilian infrastructure is not the worst thing; there are much more serious threats.
Computer viruses as a strategic weapon
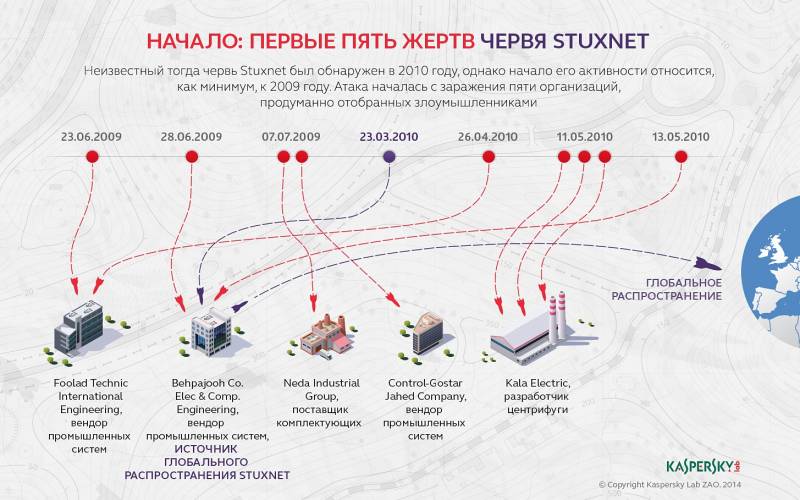
June 17, 2010 for the first time in stories The win32 / Stuxnet virus was discovered - a computer worm that infects not only computers running the Microsoft Windows operating system, but also industrial systems that control automated production processes. The worm can be used as a means of unauthorized data collection (espionage) and sabotage in automated process control systems (APCS) of industrial enterprises, power plants, boiler houses, etc. According to leading experts and companies working in the field of cybersecurity, this virus is the most complex software product, on the creation of which a professional team of several dozen specialists worked. In terms of complexity, it can be compared to the Tomahawk cruise missile, only designed for operations in cyberspace. The Stuxnet virus has caused some of the uranium enrichment centrifuges to fail, slowing the pace of progress in Iran's nuclear program. The Israeli and US intelligence agencies are suspected of developing the Stuxnet virus.
Later, other computer viruses were discovered, similar in complexity to production with win32 / Stuxnet, such as:
- Duqu (alleged developer Israel / USA) - designed to discreetly collect confidential data;
- Wiper (alleged developer Israel / USA) - at the end of April 2012 destroyed all information on several servers of one of the largest oil companies in Iran and completely paralyzed its work for several days;
- Flame (alleged developer Israel / USA) is a spy virus, supposedly developed specifically for attacks on Iranian computer infrastructure. Can identify mobile devices with a Bluetooth module, track location, steal confidential information and eavesdrop on conversations;
- Gauss (alleged developer Israel / USA) - aims to steal financial information: e-mail, passwords, bank account data, cookies, as well as system configuration data;
- Maadi (alleged developer Iran) - is able to collect information, remotely change computer parameters, record sound and transmit it to a remote user.
Thus, we can conclude that in some countries, professional development teams have already been formed, which put the production of cybernetic weapons... These viruses are the first "swallows". In the future, on the basis of the experience gained by the developers, much more effective means of cyber warfare will be created (or have already been created), capable of causing enormous damage to the enemy.
Features and perspectives
It is necessary to clearly understand the key feature of cyber weapons - their anonymity and secrecy of use. You can suspect someone, but it will be extremely difficult to prove his involvement in the use. The creation of cyber weapons does not require the movement of physical objects across national borders - the strike can be struck by anyone, at any time. The situation is aggravated by the lack of legal norms for the conduct of warfare in cyberspace. Malware can be used by governments, corporations, or even organized crime.
Each programmer has a certain style of writing code, by which he, in principle, can be recognized. It is possible that attention is already being paid to this problem in the corresponding structures, there are some specialists or special software - "modifiers" of the code, "depersonalizing" it, or, conversely, making it look like the code of some other programmers / structures / services / companies , in order to "substitute" them for the role of a malware developer.
Malicious software can be roughly divided into "peacetime" and "wartime" viruses. The former must act unnoticed - mining data, reducing the efficiency of the enemy's industry. The second is to act extremely quickly and aggressively, openly inflicting maximum damage in a minimum period.
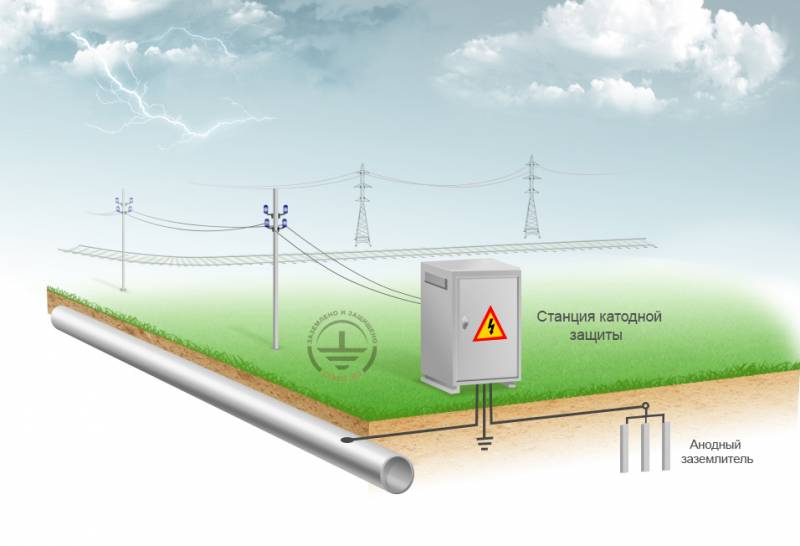
How can a peacetime virus work? For example, underground steel pipelines / gas pipelines are equipped with so-called cathodic protection stations (CPS), which prevent pipe corrosion by means of a potential difference across them and on a special electrode. There was such a case - in the 90s, at one of the Russian enterprises, the lights were turned off at night (to save money). Together with the lighting and equipment, the SKZs protecting the underground infrastructure were turned off. As a result, all underground pipelines were destroyed in the shortest possible time - rust formed at night, and during the day it peeled off under the influence of the SCZ. The cycle was repeated the next day. If the SCZ did not work at all, then the outer layer of rust for some time itself would serve as a barrier to corrosion. And so - it turned out that the equipment designed to protect pipes from corrosion, itself became the cause of accelerated corrosion. Considering that all modern equipment of this type is equipped with telemetry means, it can potentially be used for a targeted attack by the enemy of underground pipelines / gas pipelines, as a result of which the country will suffer colossal economic damage. At the same time, malware can distort telemetry results by hiding its malicious activity.
An even greater threat is posed by foreign equipment - machine tools, gas turbines, and more. A significant part of modern industrial equipment requires a continuous connection to the Internet, including in order to exclude its use for military needs (if such was the delivery condition). In addition to the ability to block our industry, for the most part tied to foreign machines and software, a potential adversary may be able to download programs for the manufacture of products directly from "their" machines, in fact, getting even more than just blueprints - manufacturing technology. Or the opportunity at a certain moment to give the command to start "chasing" a marriage, when, for example, every tenth or one hundredth product is defective, which will lead to accidents, falling missiles and planes, layoffs, criminal cases, search for the guilty, failure of contracts and state defense orders.
Serial production of cyber weapons
No war can be only defensive - defeat in this case is inevitable. In the case of cyber weapons, Russia needs to not only defend itself, but also attack. And the creation of cyber troops will not help here - it is precisely the "plant" for the serial production of malicious software that is needed.
According to the data circulating in the public domain and in the media, it can be concluded that the creation of cyber weapons is currently being carried out by the relevant units of special services and law enforcement agencies. This approach can be considered incorrect. Not a single branch of the armed forces is independently engaged in the creation of weapons. They can issue terms of reference, control and finance the creation of new types of weapons, and assist in their development. However, the enterprises of the military-industrial complex are directly involved in the creation of weapons. And as noted earlier, the latest examples of cyber weapons, such as the Stuxnet, Duqu, Wiper, Flame, Gauss viruses, can be compared in complexity to modern high-precision weapons.
Take the Stuxnet virus as an example - to create it requires specialists in a wide variety of fields - specialists in operating systems, communication protocols, information security, behavioral analysts, electric drive specialists, specialized centrifuge control software, reliability specialists, and many others. Only in a complex can they solve the problem - how to create a virus that can get to a specially protected facility that is not connected to an external network, detect the required equipment and, imperceptibly changing its operating modes, disable it.

Centrifuges for uranium enrichment are the most complex expensive equipment, which, as practice has shown, can be disabled without anti-bunker bombs and cruise missiles.
Since the targets of cyber weapons can be completely different industries, infrastructure facilities, equipment and weapons, the conditional "plant" for the serial production of cyber weapons will include dozens and hundreds of different departments, hundreds or even thousands of specialists. In fact, this task is comparable in complexity with the development of nuclear reactors, rocket or turbojet engines.
A few more points can be noted:
1. Cyber weapons will have a limited life. This is due to the rapid development of the IT industry, the improvement of software and means of its protection, as a result of which vulnerabilities used in a previously developed sample of cyber weapons can be closed.
2. The need to ensure control over the zone of distribution of a sample of cyber weapons to ensure the security of their own facilities. At the same time, it should be borne in mind that excessive limitation of the zone of distribution of a sample of cybernetic weapons can indirectly indicate its developer, just as the predominant spread of the Stuxnet virus in Iran's nuclear infrastructure indicates Israel and the United States as possible developers. On the other hand, one cannot fail to note the opening opportunity to deliberately discredit a potential adversary.
3. Possibility of high-precision application (according to tasks) - reconnaissance, distribution / destruction of information, destruction of specific elements of infrastructure. At the same time, one sample of cybernetic weapons can be focused simultaneously on solving several problems.
4. The range of goals and objectives solved by cyber weapons will constantly expand. It will include both traditional tasks for the extraction of information and the tasks of information countermeasures (propaganda), physical destruction or damage to technological equipment. The high rates of informatization of human society will increase the feasibility of developing cyber weapons as an asymmetric response to the development of expensive high-precision, hypersonic and space weapons systems by the enemy. At a certain stage, cyber weapons can compare in their impact potential with strategic weapons.
5. Ensuring the security of the national IT infrastructure is impossible without gaining experience in creating cyber weapons. It is the creation of offensive cyber weapons that will allow identifying potentially vulnerable spots in the national IT infrastructure and defense systems (this is especially important given the introduction of digital automated combat control systems).
6. Taking into account the fact that the development and use of cyber weapons must take place continuously, including in a conditionally "peacetime", it is necessary to ensure the highest level of secrecy. At the same time, the development of cyber weapons does not require the physical creation of huge factories, the purchase of equipment, the manufacture of a large range of components, the acquisition of rare or expensive materials, which simplifies the task of ensuring secrecy.
7. In some cases, the introduction of malware should be carried out in advance. For example, the Iranian network to which the centrifuges were connected was isolated from the Internet. However, having provided the ability to download the virus through intermediate media, the attackers ensured that a negligent employee (or a sent Cossack) carried it to the internal network on a flash drive. It takes time.
Application examples
Let us take as an example the conditional state in the Middle East, the largest producer of reduced natural gas (LNG), whose interests began to seriously contradict the interests of the Russian Federation.
The considered state possesses a network of oil and gas pipelines, technological lines for the production of LNG, as well as fleet tankers of "Q-Flex" and "Q-Max" class intended for LNG transportation. On top of that, a US military base is located on its territory.
A direct armed attack on the country in question can do more harm than good. So, limit yourself to a diplomatic dive? The answer may be the use of cyber weapons.
Modern ships are becoming more and more automated - we are talking about fully autonomous tankers and container ships. No less automation is used in LNG plants. Thus, specialized malware loaded into the control system of Q-Flex and Q-Max tankers, or their LPG storage systems, theoretically allows at a given time (or on an external command, if there is a network connection) arrange an artificial accident with complete or partial destruction of the indicated ships. It is highly likely that there are vulnerabilities in the technical processes for the production of LNG, which will make it possible to disable the plant, including with the possibility of its destruction.

An explosion of an LNG tanker as a result of an accident at the entrance to the port or a malfunction of the LNG storage equipment can lead not only to the death of the ship itself, but also to damage to the coastal infrastructure.
Thus, several goals will be achieved:
1. Undermining the authority of the conditional state as a reliable supplier of energy resources with the subsequent possible reorientation of consumers to the Russian natural gas market.
2. Growth of world prices for energy resources, allowing to receive additional funds for the federal budget.
3. Decrease in the political activity of the conditional state and interference in the internal affairs of other states in the region, due to a decrease in its financial capabilities.
Depending on the economic damage inflicted, a complete change of the ruling elite can occur, as well as a transition to a limited conflict between the conditional state and its neighbors, who may wish to take advantage of the weakness of their neighbor to change the balance of power in the region.
The key to this operation is the issue of secrecy. Can Russia be directly blamed if there is no clear evidence? Unlikely. The conditional state is full of enemies and competitors. And their ally, the United States, has been repeatedly seen in conducting hostile operations against even the most loyal of them. Maybe they needed to inflate prices to support their mining companies using expensive hydraulic fracturing? Nothing personal - just business ...
Another option for the use of cyber weapons was suggested by a recent incident. A huge vessel - a tanker or container ship, passes a narrow channel, suddenly the control system gives a series of sharp commands to change the course and speed of movement, as a result of which the vessel turns sharply and blocks the channel, completely blocking it. It may even tip over, making the operation to remove it from the canal extremely time-consuming and costly.

The Evergreen Group container ship that blocked the Suez Canal showed how the blockage of transport arteries affects the global economy
In the absence of clear traces of the culprit, it will be extremely difficult to establish - anyone can be blamed for this. It will be especially effective if such incidents occur simultaneously in several channels.
Thus, the development of industrial-scale cyber weapons is a high priority. Information technology, along with nanotechnology and biotechnology, is the cornerstone of dominance in the XNUMXst century. At the same time, its development will cost orders of magnitude cheaper - both the development of promising nano-biotechnologies and conventional modern weapons.



Information