Keepers of secrets

For centuries, ciphers have been used to preserve secrets. One of the most ancient cipher systems, the information about which is brought to us story, is a wander. It was used by the ancient Greeks in the fifth century BC. In those days, Sparta, supported by Persia, waged war against Athens. Spartan commander Lysander began to suspect the Persians in a double game. He urgently needed true information about their intentions. At the most critical moment of the Persian camp arrived slave-messenger with an official letter. After reading the letter, Lysander demanded a belt from the rider. It turns out that on this belt a true friend (now we would say “secret agent”) Lysandra wrote an encrypted message. Various letters were written in disorder on the belt of the messenger, which did not add up to any words. Moreover, the letters were not written along the belt, but across. Lysander took a wooden cylinder of a certain diameter (wandered), wrapped the belt of the messenger in such a way that the edges of the belt's turns closed, and on the belt a message lined up along the cylinder lined up which he was waiting for. It turned out that the Persians were plotting to inflict an unexpected stab on the back of the Spartans and killed the supporters of Lysander. Having received this message, Lysander unexpectedly and covertly landed near the location of the Persian troops and with a sudden blow defeated them. This is one of the first known case histories in which encryption played a crucial role.

It was a permutation cipher, the ciphertext of which consists of letters of plaintext permuted according to a certain, but not known, extraneous law. The cipher system here is a permutation of the letters, actions are the winding of the belt on the wander. The cipher key is the diameter of the wanderings. It is clear that the sender and recipient of the message must have wanders of the same diameter. This corresponds to the rule that the key during encryption must be known to both the sender and the recipient. Skital is the simplest type of cipher. It is enough to pick up a few wanderings of various diameters, and after winding the belt on one of them would be a clear text. This encryption system was decrypted in ancient times. The belt was wound on a conical wander with a small taper. Where the cross-sectional diameter of the conical skitals is close to the diameter used for encryption, the message is partially read, after which the belt is wound on the wander of the desired diameter.
He used a different type of cipher (replacement cipher) by Julius Caesar, who is even considered the inventor of one of these ciphers. The idea of Caesar's cipher was that on paper (papyrus or parchment) two alphabets of the language are written one under another, in which the message will be written. However, the second alphabet is written under the first with a definite (known only to the sender and the recipient, the shift). For the Caesar cipher, this shift is equal to three positions. Instead of the corresponding letter of the plaintext, which is taken from the first (upper) alphabet, the sign of the lower alphabet under the letter is written in the message (ciphertext). Naturally, now such a cipher system is elementarily opened even by a non-specialist, but at that time Caesar's cipher was considered untransferable.
The Greeks invented a somewhat more complex cipher. They wrote out the alphabet in the form of a table of size 5 x 5, denoted by symbols with rows and columns (ie, they were numbered) and instead of the letter of the plaintext two symbols were written. If these symbols are issued in a message as a single block, then with short messages on one particular table, such a cipher is very resistant even by modern concepts. This idea, which is about two thousand years old, was used in the complex codes of the First World War.
The collapse of the Roman Empire was accompanied by the decline of cryptography. History has not retained any noticeable information about the development and application of cryptography in the early and middle Middle Ages. And only a thousand years later, cryptography is being revived in Europe. The sixteenth century in Italy is a century of intrigue and conspiracy. The Borgia and Medici clans are fighting for political and financial power. In such an atmosphere, ciphers and codes become vital.
In 1518, Abbot Trithemius, a Benedictine monk who lived in Germany, published a book in Latin called “Printing”. It was the first book on the art of secret writing, and soon it was translated into French and German.
In 1556, the doctor and mathematician from Milan Girolamo Cardano published a work describing the encryption system he invented, which went down in history as the Cardano lattices. It is a piece of hard cardboard with holes cut in a random order. Cardano's lattice was the first use of the permutation cipher.
It was considered an absolutely stable cipher even in the second half of the last century, with a sufficiently high level of mathematics development. So, in the novel by Jules Verne "Matias Shandor" dramatic events develop around the cipher letter sent with a pigeon, but accidentally falling into the hands of a political opponent. In order to read this letter, he entered as a servant to the author of the letter in order to find a cipher grid in his house. In the novel, no one has the thought of trying to decrypt a letter without a key, based only on the knowledge of the applied cipher system. By the way, the intercepted letter was in the form of an 6 x 6 alphabetic table, which was a cryptographic blunder. If the same letter were written in a line without spaces and the total number of letters using the addition did not equal 36, the decryptor would still have to test hypotheses about the encryption system used.
You can count the number of encryption options provided by the 6 x 6 Cardano lattice. If you solve the problem "in the forehead" (sort through all possible options and try to read the plaintext), then even checking one option per second and continuously working 24 hours a day, you will have to decipher such a grid for several tens of millions of years! Invention Cardano was extremely tenacious. On its basis, during the Second World War, one of the most resistant naval ciphers of Great Britain was created.
However, to date, methods have been developed that allow, under certain conditions, to decipher such a system fairly quickly.
The disadvantage of this lattice is the need to reliably hide the lattice from outsiders. Although in some cases it is possible to remember the location of the slots and the order in which they are numbered, but experience shows that it is impossible to rely on a person’s memory, especially with rare use of the system. In the novel Mathias Shandor, the transfer of the grid into the hands of the enemy had the most tragic consequences for the author of the letter and for the entire revolutionary organization of which he was a member. Therefore, in some cases, less robust, but simpler encryption systems that are easily recovered from memory may be preferable.
The title of "father of modern cryptography" with the same success could claim two people. This is the Italian Giovanni Battista Porta and the Frenchman Blaise de Vigener.
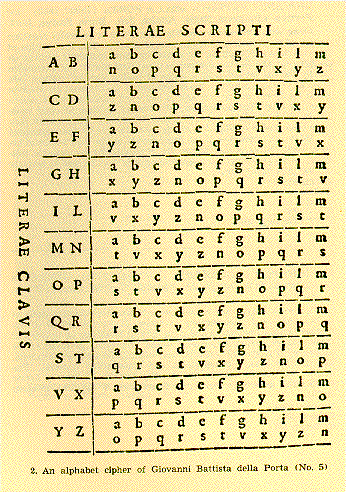
In the 1565 year, Giovanni Porta, a mathematician from Naples, published a replacement-based cipher system that allowed any plaintext character to be replaced with a cipher-book with eleven different ways. To do this, 11 cipher alpha is taken, each of them is identified by a pair of letters, which determine which alphabet should be used to replace the letter of the plaintext with the cipher alphabet. When using cryptographs Ports, in addition to the presence of 11 alphabets, you also need to have a keyword defining the corresponding code alphabet at each encryption step.
Usually the ciphertext in the message is written together. On the technical lines of communication, it is usually transmitted in the form of five-digit groups separated by a space of ten groups in a row.
The Ports system has a very high resistance, especially with arbitrary selection and writing of alphabets, even according to modern criteria. But it also has drawbacks: both correspondents must have rather cumbersome tables that must be kept from prying eyes. In addition, you need to somehow agree on a keyword that must also be secret.
These problems were solved by the diplomat Vizhener. In Rome, he became acquainted with the works of Trithemia and Cardano, and in 1585 he published his work The Treatise on Ciphers. Like the Ports method, the Vigenère method is based on a table. The main advantage of the Vigenera method is its simplicity. Like the Ports system, the Vigenere system requires a keyword (or phrase) to encrypt, the letters of which determine by which 26 cipher alphabets each specific letter of the plaintext will be encrypted. The letter of the key text defines the column, i.e. concrete cipherphrase. The letter of the ciphertext is inside the table corresponding to the letter of the plaintext. The Visioner system uses all 26 encryption and is inferior in performance to the Ports system. But the Vigenere table is easily restored from memory before encryption, and then destroyed. The resilience of the system can be enhanced by agreeing not on a key word, but on a long key phrase, then the period of using cipher-alpha will be much more difficult to determine.

All encryption systems until the twentieth century were manual. With a weak ciphering intensity, this was not a drawback. Everything changed with the advent of telegraph and radio. With the increase in the intensity of the exchange of cipher communications via technical communication means, the access of unauthorized persons to the transmitted messages was greatly facilitated. Requirements for the complexity of ciphers, the speed of encryption (decryption) of information have increased dramatically. There was a need to mechanize this work.
After the First World War, the rapid development of the encryption business begins. New cipher systems are being developed, machines are invented to speed up the process of encryption (decryption). The most famous was the Hagelin mechanical cipher. The company for the production of these machines was founded by the Swede Boris Hagelin and still exists. Hagelin was compact, easy to use, and provided high cipher strength. This cipher machine implemented the replacement principle, and the number of cipher-alphabets used exceeded that of the Ports system, and the transition from one cipher-alphabet to another was carried out in a pseudo-random manner.

Technologically, the operation of the machine used the principles of work of automatic machines and mechanical automatic machines. Later, this machine has undergone improvements, both in mathematical and mechanical terms. This significantly increased the system durability and usability. The system was so successful that when switching to computer technology, the principles embodied in Hagelin were modeled electronically.
Another option for implementing the replacement cipher is disk machines, which have been electromechanical since their introduction. The principal encryption device in the car was a set of disks (from 3 to 6 pieces), planted on one axis, but not rigidly, and so that the disks could rotate around the axis independently of one another. The disk had two bases made of bakelite, into which contact terminals were pressed according to the number of letters of the alphabet. In this case, the contacts of one base were electrically internally connected to the contacts of the other base in pairs in an arbitrary way. The output contacts of each disk, with the exception of the latter, are connected through fixed contact plates to the input contacts of the next disk. In addition, each disk has a flange with protrusions and valleys, which together determine the nature of the stepping movement of each disk on each encryption cycle. At each clock cycle, encryption is performed by pulsing the voltage through the input contact of the switching system corresponding to the letter of the plaintext. At the output of the switching system, the voltage appears on the contact, which corresponds to the current letter of the ciphertext. After the implementation of one encryption cycle, the disks are independently rotated one or more steps (at the same time, some disks in each particular step may be completely idle). The law of motion is determined by the configuration of disk flanges and can be considered pseudo-random. These machines were very widely distributed, and the ideas embodied in them were also modeled electronically during the era of electronic computers. The durability of the ciphers produced by such machines was also exceptionally high.

During the Second World War, the Enigma disk machine was used to encrypt Hitler's correspondence with Rommel. One of the cars for a short time fell into the hands of British intelligence. Having made an exact copy of it, the British got the opportunity to decrypt secret correspondence.
This question is relevant: is it possible to create an absolutely strong cipher, i.e. one that would not even open theoretically. Cybernetics father Norbert Wiener stated: “Any sufficiently long piece of ciphertext can always be decrypted, provided that the opponent has enough time for this ... Any cipher can be decrypted, if only it is an urgent need and the information you expect to get is worth it means of effort and time. " If we are talking about a cipher generated in accordance with any precisely and unambiguously determined algorithm, no matter how complicated it is, then this is indeed the case.
However, the American mathematician and information processing specialist Claude Shannon showed that an absolutely strong cipher could be created. At the same time there is no practical difference between an absolutely strong cipher and so-called cipher codes (realized with the help of specially developed complex algorithms). An absolutely strong cipher should be generated and used as follows:
- the cipher is not generated using any algorithm, but completely randomly (throwing a coin, opening a card at random from a well-mixed deck, generating a sequence of random numbers using a random number generator on a noise diode, etc.);
- the length of the ciphertext should not exceed the length of the developed cipher, i.e. A single cipher character must be used to encrypt a single plaintext character.
Naturally, all the conditions for correct handling of ciphers should be fulfilled and, above all, it is impossible to re-encrypt the text with the cipher once used.
Absolutely strong ciphers are used in cases where the absolute impossibility of decrypting the correspondence by the enemy must be guaranteed. In particular, such ciphers are used by illegal agents acting on the territory of the enemy and using cipher block notes. A notepad consists of pages with columns of numbers selected completely randomly and called block cipher.

The encryption methods are different, but one of the easiest is the following. The letters of the alphabet are numbered in two-digit numbers A - 01, B - 02 ... I - 32. Then the message “Ready for meeting” looks like this:
plain text - READY FOR THE MEETING;
open digital text - 0415191503 11 03181917062406;
block cipher - 1123583145 94 37074189752975;
Ciphertext - 1538674646 05 30155096714371.
In this case, the ciphertext is obtained by the significant addition of the open digital text and the block cipher modulo 10 (that is, the transfer unit, if any, is not taken into account). The ciphertext, intended for transmission via technical means of communication, has the form of five-digit groups, in this case it should be: 15386 74648 05301 5509671437 16389 (the last 4 digits are written arbitrarily and are not taken into account). Naturally, it is necessary to notify the recipient which page is used cipher block. This is done in a prearranged place in plain text (numbers). After encryption, the used cipherblock page is pulled out and destroyed. When decrypting the received cryptogram from the ciphertext, the same cipher must be subtracted by the 10 module. Naturally, such a notebook should be kept very well and secretly, since the very fact of its presence if it becomes known to the enemy means failure of the agent.
The arrival of electronic computing devices, especially personal computers, meant a new era in the development of secret writing. Among the many advantages of computer-type devices are the following:
a) extremely high speed of information processing,
b) the ability to quickly enter and encrypt previously prepared text,
c) the possibility of using complex and extremely strong encryption algorithms,
d) good compatibility with modern means of communication,
e) fast text visualization with the possibility of its fast printing or erasing,
e) the possibility to have different encryption programs with access lock on one computer
unauthorized persons using a password system or internal cryptographic protection,
g) universality of encrypted material (i.e., under certain conditions, a computer encryption algorithm can encrypt not only alphanumeric information, but also telephone conversations, photographic documents and video materials).

However, it should be noted that the organization of information security in its development, storage, transmission and processing should follow a systematic approach. There are many possible ways to leak information, and even good cryptographic protection does not guarantee its security, unless other measures are taken to protect it.
Использованная литература:
Adamenko M. Fundamentals of classical cryptology. Secrets of ciphers and codes. M .: DMK press, 2012. C. 67-69, 143, 233-236.
Simon C. The Book of Ciphers. M .: Avanta +, 2009. C. 18-19, 67, 103, 328-329, 361, 425.
Information