"The Naked King"
The deplorable situation, the state power, in the person of the first persons, began to be understood only after the secret information was discharged by the notorious Snowden, he is the boy who pointed out the obvious.
And he uttered the sacred words that the leaders of the country finally heard.
Professionals know what is happening now in the relevant state structures. As always with us, campaigning reaches marasmus, but it “shakes” coolly, threatens with organizational leads and landings.
I will not say anything more on global themes, otherwise I will be “carried” like the unforgettable Ostap. Let me turn to a concrete example, I hope everyone, even non-professionals, everything will become obvious.
Business in Russian
At one time, I stumbled upon an article in Komsomolskaya Pravda, “Do Spyware Notebooks Are Delivered to Russia?”, It was about the Getac A790 protected notebook by the Taiwanese company Getac Technology.
Here is this "handsome":

The article talked about the presence on this computer of the pre-installed program Computrace LoJack, developed by Canadian firm Absolute Software. It was argued that the program comes in activated form and immediately tries to connect to servers in Canada. In addition, the manufacturer has stimulated sellers of equipment in Russia to provide it with forward information about customers of data protected computers.
In conclusion, an unequivocal conclusion was made about the target action of a potential adversary and it was argued that these computers are widely used in the Russian armed forces ....
After reading the article in Komsomolskaya Pravda, I immediately recalled a three-year-old material devoted to the same program on rom.by: “The BIOS Trojan from Absolute Software”. It described in detail the mechanism for locating and working in the BIOS of the program module of this program, so the topic is not new.
Interested in visiting the developer’s website and reading, really, the program sends geolocation data to a remote server, has the ability to remotely lock a computer and erase information from disks by commands from Absolute Software’s servers. In addition, it is possible to complete a cycle of remote laptop management starting from updating the BIOS, installing, removing any programs and ending with reinstalling the OS. The official purpose of the program is to prevent data leakage and the use of a laptop in case of its theft or loss.
The software part of the Computrace LoJack system consists of two modules, the first one is written into the BIOS at the computer production stage, and the second is loaded from the network in case the computer owner decides to use the Computrace LoJack program. And this service is not free, you need to pay about $ 50 for a one-year subscription to the services of Absolute Software.
Altruism is not peculiar to business, free activation of a paid service suggests that the benefit obtained from this justifies financial costs (it does not mean free of charge for free). Who pays for the information I think is also understandable ...
Looking at the image of the protected notebook Getac А790 immediately remembered about a similar gray box seen on the site of one of the customers, it was pushed into a corner, covered in dust, and had not been used for a long time. I wanted to “touch” the machine myself and in the next visit to this customer immediately went to the dusty box that interested me.
I open and do not believe my eyes, this is not a Getac A790 notebook, judging by the nameplate on the front panel, this is the Russian computer MVK-2, moreover, on the label all the data about the model and the manufacturer, where it is written that this product was manufactured by InfoPro in 2010. In addition, the holographic sticker of special inspection flaunts on the laptop.
For those who do not know, I will explain, special inspection and special investigations are necessary procedures (and very expensive) for the equipment to appear on secret objects and in the troops. After these checks, the equipment is considered safe in terms of leakage of secret and confidential information and can be used on secret and protected objects.
The box was intrigued and I simply could not turn it on, my hands reached out for the keyboard, turned on, the initialization screen appeared on the screen and everything fell into place right away - the classic version of “business in Russian”.
The Russian company, which calls itself the developer and manufacturer of MVK-2 (InfoPro), did not even bother to register its own initialization graphic screensaver in BIOS and the name Getac А2 proudly appears on the Russian computer MVK-790.
I was not lazy and filmed this "miracle" on my mobile phone, here it is.
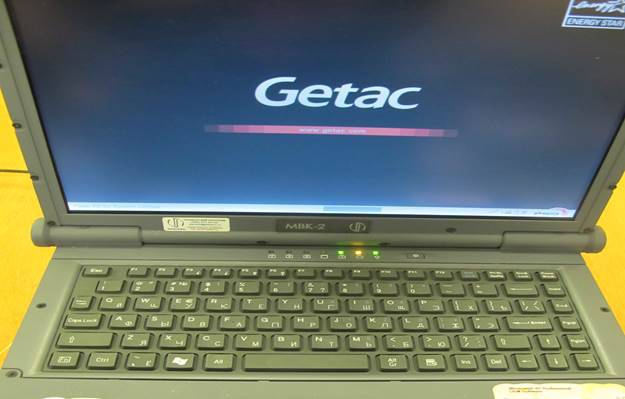
Immediately it became even more interesting, MVK-2 is not some kind of “left” Getac А790 for you. MVK-2 is a Mobile Computing Complex, - the main protected computer of the Armed Forces of Russia, domestic development, in the army there are thousands, if not tens of thousands ...
Well, about the domestic development and national assembly, it all became clear to me right away, but if there are any Absolute Software programs after special investigations (as indicated by a holographic sticker), I was interested in the Absolute Software program. Taking advantage of free time, without even asking the customer (I confess, is a sinner), I scanned BIOS for the signature of the Computrace LoJack program, which I took from an article on rom.by. And I was not surprised when I found them there. InfoPro engineers from the BIOS of their computers did not delete anything, and all the special studies did not reveal the presence of this official "bookmark" in MVK-2.
The bluntness and impudence of the “manufacturer” is amazing, there are official programs for assembling / disassembling BIOS, can any module from BIOS be removed or inserted without problems, which prevented InfoPro specialists from inserting their own screensaver and cutting the scandalous module from BIOS? This procedure was mastered by all domestic collectors, it is not unique ...
"Singed" chips
Unfortunately, the machine was not connected to the Internet or to the local network, so it was not possible to look at the network activity on the IP addresses to find out the state of the Absolute Software service.
The only thing that did was photographed the screens of the device manager in the Sandra program in order to deal with the equipment inside MVK-2 at leisure. There was a feeling that $ 50 bucks for the activation of the Computrace LoJack program is paid for a reason, there are still “miracles” in this thing.
Here is a photo of the screen that interested me specifically:
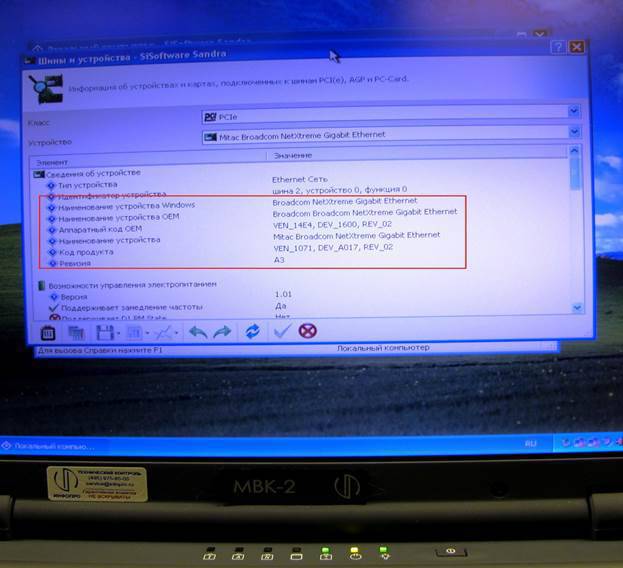
Broadcom network chips installed at MVK-2 have long enjoyed ill fame as potential sites for bookmarking. According to the manufacturer codes came out on a specific chip Broadcom BCM 5752.
The company Broadcom has a whole line of chips from the BCM 57xx series. The chips of this family lit up on many hacker sites, even our domestic magazine Hacker wrote at least twice last year about bookmarks on these chips.
There was an article “Rootkit in a network card: a programmer’s fantasies about creating an invincible rootkit” and a more specific news With reference to the successful exploit: "Rootkit in the network map." So, the VSM 57xx chips are used by hackers for a long time, this is no secret.
The VSM 57xx series chips have their own flash memory (you can also connect external flash memory on a dedicated SPI interface), its own RAM, and its own RISC processor.
Here is the official block diagram of the BCM 5752 chip used in the MC-2:
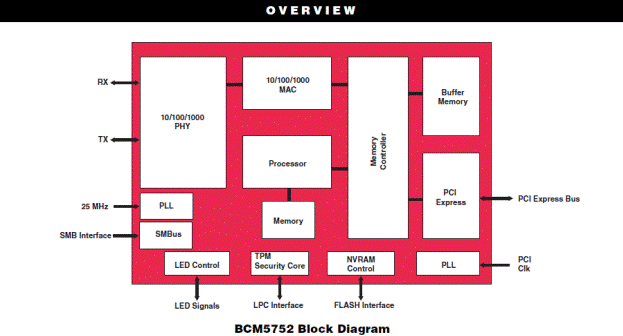
In fact, this is a computer in a computer, and programs that are flashed inside its flash memory are executed both on its own embedded RISC processor and on the central processor of the computing unit during system initialization (advanced BIOS on peripheral controllers).
According to the documentation, there are only 16Kbytes of flash memory inside the chip, but on the external interface you can place additional up to 8Mbytes of programs and data. Imagine how much you can "stuff" there?
In conjunction with the program Computrace LoJack, such a network chip can do anything. You can find out the contents of the flash memory of this chip only on the tool stand, and it’s not a fact that it will work out. I again began an attack of spy mania, but not virtual, but networked.
The severity of the laws and the lack of their enforcement
I look closely at the chip's block diagram, I can say I’m drilling it with my eyes, and finally it comes to me - TPM Security Core is the same TPM module! I look in the documentation and exactly, there is a built-in TPM module in the VSM 5752 chip from this family 1.2 standard connected to the LPC interface.
The presence of a module TRM in the Russian protected computer is nonsense, it is legally forbidden even to import equipment with such modules, and using them in military equipment is generally a matter of jurisdiction. The only option, the chip may be present on the board, but must be physically disabled at the production stage and be in an inoperable (de-energized) state.
Formally, the ban is based on the use of foreign-developed cryptographic algorithms in these TPM modules. The true reason for the ban is that TPM modules are a means of generating and storing encryption keys and passwords with a unique key (PRIVEK) for the root of the trust chain, which is the root encryption key for the RSA algorithm (its secret part).
Chip makers know this key, and in theory, no one else. But all manufacturers of crypto-tools have contacts with special services without fail, I think it is not necessary to explain who will keep duplicates of these keys?
Knowledge of the root key for a particular TPM module allows deciphering the contents of the TPM module memory and, moreover, always accurately localize the location of a particular computing installation in the network space.
I wanted to check for the presence of TPM module activity on MVK-2, it was easy to do, for this there are two possibilities. In system ASPI tables there is a special object that describes the presence of a TPM module, but this is only a mark in memory. The device may be present, and the records in the tables about its presence may not be.
So this method is not reliable enough if there are no records in the system tables, the OS will not see it either.
The second method is much more reliable, any device interacts with other components of the computing system through registers, if these registers are active (you can read them and write information in them) then the device is operational. The idea is that the module that is disabled in the production conditions of the TPM does not have workable registers. It's simple to check, all the TPM registers of the 1.2 standard module are on the system bus in the fixed address space 0FED4_0000h - 0FED4_FFFFh, it was not me who invented it, it is written in the standard.
Again, including the MVK-2 being investigated, I already had a program on hand to view the registers on the system bus (of my own production, of course), and was not at all surprised to find out the activity of the TPM module.
What happens if you do not comply with the laws
The expected result was confirmed, the TPM registers of the module were in working condition, so no one disconnected the TPM module chip. Only here the information in the registers did not meet the specifications. In one of the active registers, scan-codes of keystrokes were found ...
It seemed that the information about the scan code of the last key pressed is stored in the module's TPM registers, and this already resembled what is in a professional language called hardware bookmark, the keylogger.
Is it possible? It is quite possible, since the keyboard controller and the TPM module are located on the same interface — the LPC — and this interface is made according to the scheme of the serial connection of all devices connected to it. In fact, the TPM module was turned into a sniffer, listening to the bus and storing information in its registers from the keyboard. Thus, hacker technologies, which have been discussed at professional forums for more than a year, are now figuratively speaking in the service of some kind of special services.
The hardware keylogger in MVK-2 is “cool”, may I be mistaken - of course, since this is a preliminary result of external research. If you could get inside this machine, you can either prove it or disprove, in any case, you need to understand, but I have no such possibility.
A logical question, and maybe someone has already figured out and came to the conclusion that everything is normal, - you can work?
I doubt that experts who are not able to change the screensaver in BIOS, who do not know about the tab in the BIOS of the Computrace LoJack program, hardly even know anything about the TPM modules, not to mention understanding their specifications.
So this untested equipment continues to flow into Russia under the proud name “Mobile Computing Complex MVK-2” and carries on its board an obvious tab in BIOS and a hardware keylogger in a network chip. And these complexes are completed with very important objects and products, here is one of the examples downloaded from the Internet:


State secret as a commodity
And in conclusion, I still can not refrain from global generalizations, they are sad.
In our country, security has become a commodity that is being traded, no one has got. In order not to be unsubstantiated, I’ll give a specific screenshot of the site of one of the many intermediaries who make money at the state secret:
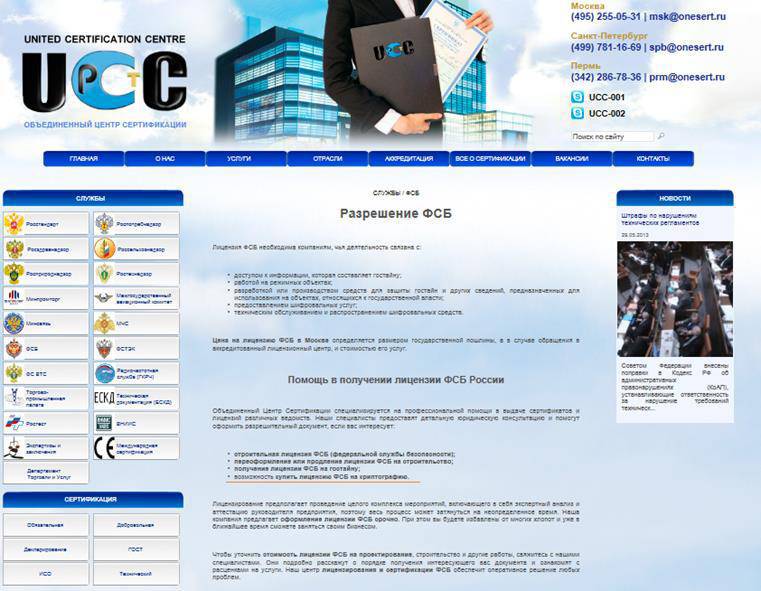
Especially touching is the frankness of the wording of the text on the site, such as "The ability to buy a license from the FSB for cryptography", it is highlighted in red on the screenshot. And this is not a reservation, it once again slipped the "Naked Truth" about the "Naked King".
What has long been talked about in smoking rooms (that the employees of the FSB 8 center turned the issuance of licenses into a “business in Russian”) found such visual, independent, public confirmation.
It's sad, gentlemen ...
PS Do not think only that the authorities do not know about this situation, not at all.
More than a year ago, everything that was written here was reported in very “high cabinets”, in particular, Deputy Prime Minister D. Rogozin was informed about this.
The result is zero, but after that I got problems, but as they say, the world is not without honest and decent people, it has passed.
Information