US Global Cybership
Unveiled by a former employee of the US National Security Agency (NSA) Edward Snowden, US espionage materials continue to haunt the world community. The peculiarity of the international scandal that broke out was that the voices of the closest allies of the United States - the countries of the European Union - joined the general stream of criticism. At the same time, as events developed, their own policy of double standards was exposed, for which we must say a special thank you to those who organized stuffing of exposing materials into world mass media.
Thus, the first reports about the hacking by Americans of the databases of major corporations, the tapping of leaders and members of the governments of Latin America were left without any comments from high-ranking officials of Western European countries. However, they did not remain silent when materials appeared that reveal the total nature of electronic surveillance of citizens of their countries. From the lips of some European leaders sounded discontent over the excessive activity of American intelligence. The essence of this discontent boiled down to the following: we understand the need for effective measures in the fight against international terrorism, but spying among friends is unacceptable. Such a restrained reaction is understandable, as the next portion of the revealing materials testified to the cooperation of European and American intelligence services in the field of electronic espionage. And only after the publication of the facts of the first persons and high-ranking officials of the European Union, the criticism of espionage activity sounded loudly.
 For the first time since the end of the Cold War, a consolidated position of a whole group of states condemning the actions of the American administration is observed. The United States is accused from the rostrum of the European Parliament of discrediting allied relations and violating the laws of European countries. Attempts by the Americans to justify reconnaissance by the need to counter terrorist threats are no longer perceived. The chairman of the European Parliament, Martin Schulz, having received information about the NSA's surveillance of deputies and their offices, made a biting statement that the European Parliament is not planning any terrorist attacks on the United States.
For the first time since the end of the Cold War, a consolidated position of a whole group of states condemning the actions of the American administration is observed. The United States is accused from the rostrum of the European Parliament of discrediting allied relations and violating the laws of European countries. Attempts by the Americans to justify reconnaissance by the need to counter terrorist threats are no longer perceived. The chairman of the European Parliament, Martin Schulz, having received information about the NSA's surveillance of deputies and their offices, made a biting statement that the European Parliament is not planning any terrorist attacks on the United States.Latin American and European politicians and officials of various levels practically in unison suggest revising or denouncing the agreements existing with the United States and introducing strict rules restricting and regulating the activities of American IT companies in their countries. In the statements of German Chancellor Angela Merkel, there is an unequivocal hint at the irreversibility of revising bilateral relations with its main strategic ally: “The foundation of trust between our countries is to be restored. And words alone are not enough for this. Changes are required. Under her initiative, a special commission of the European Union is created to investigate the circumstances of the activities of the American special services, which intends to work, including in the United States. Merkel and Brazilian President Dilma Rousseff agreed to lobby the submission of the relevant issue to the UN General Assembly and prepare a draft follow-up resolution. The government of Japan also stated the need to conduct a thorough investigation of the revealed facts of espionage.
It can be stated that the publicly wounded pride of the political leadership of a number of Western European countries has prompted them to condemn their powerful overseas friend and bring him charges of violating human rights. One can only hope that the same principles will be shown when Washington again decides in its interest to unleash an armed conflict or provoke another “color revolution”, neglecting the existing mechanisms of international security.
However, we leave it to their conscience. Back to spyware stories and note that the NSA is central to it. It has long been known that the agency is the main link of the US intelligence community in the field of electronic espionage. Materials from Edward Snowden only document the fact of total electronic surveillance of citizens of many countries.
For example, according to data published in Le Monde in Paris in October, only during 30 days - from December 10 2012 to January 8, the NSA, as part of the spyware program US2013D, intercepted more than 985 millions of telephone conversations from French citizens. The resulting information was processed and compiled into 70 million files and placed in two databases - DRTBOX and WHITEBOX. According to the newspaper, similar actions to collect information could be carried out against citizens of other countries, since spyware programs for them had a similar designation. For example, for Germany - US62,5LA and US987LB.
The number of exposing publications of this kind is growing like a snowball. On their basis, it is entirely acceptable to assert that the privacy of millions of people may be subject to American intelligence surveillance, and the information collected will be used by the United States to their advantage in near real time or wait in the wings, stored somewhere in the depths of the NSA.
Why does the United States need such a scale of electronic espionage and what goals do they have? Maybe we should agree with the opinion that nothing serious happened, they were always spying, everything and everyone, the main thing is how they manage the data obtained, and in general in the era of the information society the total eavesdropping and peeping is inevitable? In the domestic media, opinions have already emerged that, supposedly, nothing terrible happens, there have been no consequences and there will be no, everyone can relax and ignore the Snowden story. We propose to simply evaluate the known facts of espionage in relation to the strategic goals and objectives of Washington.
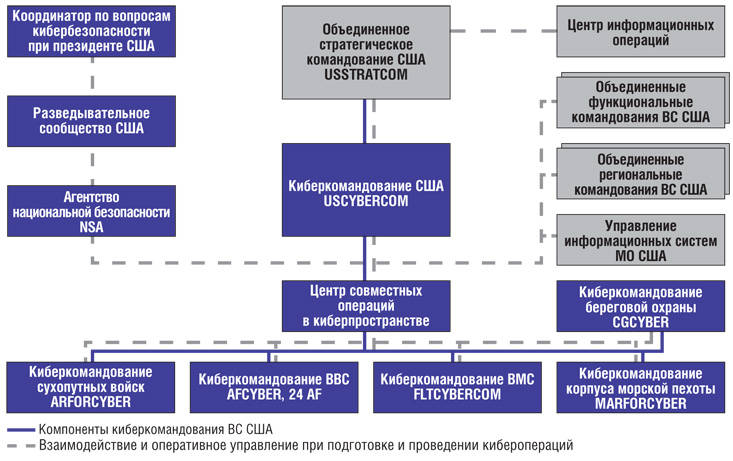
The NSA is a structural unit of the US armed forces involved in the general system of information and analytical support for the military policy of the White House. Recently, it has begun to play a key role in the implementation of a new strategic installation — winning global supremacy in cyberspace, without which, in the opinion of the US military and political leadership, it is impossible to maintain the leading position in the new century. For the first time, the tasks of preparing the armed forces for action in cyberspace were set in the US National Military Strategy 2004 of the Year. The term itself is considered as a sphere of combat operations along with land, sea and aerospace spheres and it is understood as the global area of the information environment, consisting of interconnected information and technological structures, including the Internet, telecommunication networks and computer systems, as well as embedded processors and controllers.
In accordance with the planned strategic objectives, plans for the construction and training of the American armed forces are being adjusted. After a fairly intensive check of a number of new conceptual positions, cyber command, USCYBERCOM, was created in June with the joint strategic command of the United States in June. The organization of its activities is largely based on the technological, operational and functional capabilities of the NSA. This is convincingly shown by the fact that the director of the NSA, General Keith Alexander, has been appointed as the commander of the new unit. He still combines two posts.
The interaction of the NSA and USCYBERCOM is carried out on the organization and conduct of electronic and cyber intelligence, as well as in the interests of preparing and conducting operations in the information space as a new form of use of the American armed forces, enacted by the National Military Strategy 2006 of the year.
Analysis of the content of the newly developed doctrinal documents of the US Department of Defense suggests that cyber operations are designed to solve three groups of tasks:
Such activity involves not only confrontation and suppression of the enemy in the information environment, it is also being conducted to support military, intelligence, psychological, individual specific operations.
Electronic espionage programs that have become well-known are only elements of a higher level plan pursuing the achievement of global objectives. What are these goals, one can only guess by building the relationship of cyber operations with the strategic plans of the military-political leadership of the United States and the practical steps to implement them.
Let us pay attention to the fact that, in accordance with the US founding documents, military policy is oriented towards ensuring the leading role of the United States in the conditions of the formation of a new world order. The strategic leadership, signed by President Barack Obama in January 2012, is called “Strengthening US Global Leadership. Priorities of the Ministry of Defense in the XXI Century. ” The basic concept of Armed Forces-2020, approved in September of the same year by the Chairman of the Joint Chiefs of Staff (CEC), determines the formation of abilities that will allow preemptive and demoralizing attacks on the enemy to successfully conduct operations that meet the nature of the confrontation in the new century. For this purpose, synchronization of the actions of groups of troops (forces) with the efforts of all elements of national power and more active involvement of allies and partners of the United States in joint actions are envisaged. Of particular importance is the integration of the capabilities of cybernetic forces and facilities with the capabilities of the regional combat and functional commands of the Armed Forces, as well as their interaction with other federal agencies.
It turns out that the total electronic surveillance organized by the Americans is not just an overwhelming activity of the special services and certainly not the costs of fighting international terrorism. Rather, it can be assumed that the NSA and USCYBERCOM are laying the foundations for future operations in the information environment. In particular, the mechanisms for monitoring social networks and e-mail are being perfected. This is done with the aim of tracking the socio-political situation in society and drawing up so-called social maps that reveal social connections, preferences, problems, interests, plans, location and other information about citizens in the whole state for a specific period. Combined with informational and special operations, the technology of which Americans have sufficiently worked out, this will provide great opportunities for manipulating public consciousness and using the social activity of citizens in a direction favorable to Washington. Something similar was observed quite recently in the countries of North Africa during the period of the “Arab spring”. Now it is obvious that the protest movement and the information background (twitter revolution, like in Egypt) were created in many ways artificially, including through the use of Internet technologies and social networks.
The content and nature of future wars and conflicts allows information about hacker attacks, now and then pop up in the world media. Apparently, the use of cybernetic forces and equipment can lead to serious damage - to disorganize control, disable industrial and military facilities, systems and weapon systems, disrupt vital infrastructures.
According to information from Snowden, published in Washington Post in August of this year, about 600 professional hackers work in a special unit for conducting remote access operations (Tailored Access Operations - TAO), located at the headquarters of the NSA in Fort Meade, Maryland. This deeply classified team conducts reconnaissance of the most important objects, develops technologies of cyber attacks and conducts them at the direction of the president of the country. It is assumed that the TAO team, with the participation of Israeli colleagues, developed and used the Stuxnet and Flame malicious programs to disable the database management system of Iran’s nuclear program.
The lack of data on wiretapping of domestic statesmen and citizens does not mean at all that espionage is not actually conducted. The American intelligence community has always considered us as one of the main geopolitical rivals. One can only believe that Russia has the means to counter the real and future threats to its security.
Information