The secret of the room 641А
San Francisco, California. Early morning. Over the picturesque bay, the sun disk is slowly rolling, illuminating the city hills and the Golden Gate Bridge. Through the silk California dawn the tram rumbles, the streets are filled with vehicles and hurrying passersby.
But our path lies further, to the northern part of the city, to an area called Rincon Hill.
A faceless 18-storey building with no windows and architectural delights at 611 Folsom Street, lost in the midst of similar high-rises. Close parking, lobby, elevator silently slides to the sixth floor. Winding corridors with dozens of similar doors. Personnel scurrying around everywhere - very much like a regular work day at some office center ...
But there is one door that always remains closed. Behind her is a ringing silence. No sign of life. Clerks and technicians with cups of coffee scared to run past, afraid to cast a glance in the direction of the office 641А.

Wait, there is someone there! The electronic lock clicks, and several people come out of the strange room - flawless suits, dark sunglasses, indifferent facial expressions. Without exchanging greetings with anyone, they quickly leave the building through the service entrance - a roar of the 8-cylinder Buick engine comes from the street, taking away the unknown inhabitants of the 641A room.
What happens on the sixth floor of a building on Folsom Street? Conspiracy theory? Or are shooting next
blockbuster "The Matrix"?
Okay, as long as the inside is empty, I suggest to go in and inspect the strange room. Watch out! Do not touch anything with your hands!

Strange ... It seems that there are no ghosts and portals in other worlds. Standard office, several racks with computer equipment and a cable channel coming down from the ceiling with a thick wiring harness ...
- Hands behind your head, facing the wall! On knees! You are arrested for attempting to enter US State Department property. You have the right to remain silent ...
Big brother is watching you
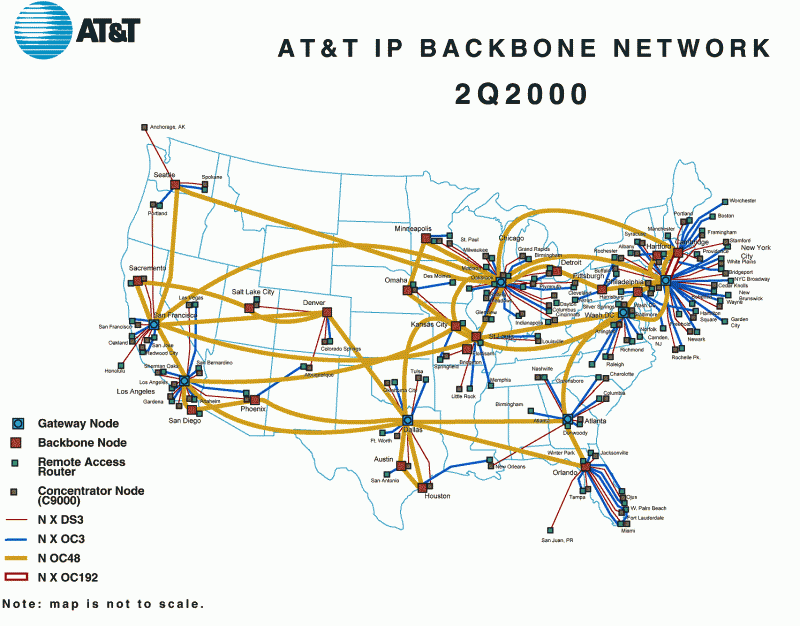
The gray building at 611 Folsom Street, San Francisco, is the largest telecommunications hub on the US West Coast, owned by AT&T, the leading telephony / internet / cable TV provider in the North American continent ...
This fact alone lends the AT&T building an air of mysticism and superstitious respect — hundreds of telephone and Internet cables from across the West Coast and the continental United States converge here; thick veins of transoceanic fiber-optic lines emerge from here - Japan, South Korea, China, Hong Kong ... Thousands of splitters, routers, servers and computers pass through their bowels millions of phone calls and thousands of gigabytes of Internet data every second.
Unsurprisingly, AT&T's Folsom Street building has come under scrutiny from the National Security Agency (NSA). The global communication center allows you to get instant access to any information of interest to the special services: interception of calls from cell and landline phones, absolute control over Internet traffic, access to information about banking transactions (cash flow, accounts and plastic cards), e-mail, social networks, etc. stock information - the entire economic, social, business and political life of a huge region of the Earth is "under the hood" of the NSA!
Project Room 641A began in 2002 when NSA officials made AT & T's management "an offer that AT&T could not refuse." On the sixth floor of the Folsom Street building, NSA personnel were allocated a cozy 48 by 24 feet (14,5 x 7 meters) space. Slightly higher, on the seventh floor, where broadband Internet channels passed, several optical splitters (beam-splitters) were installed, dividing one data stream into two identical ones - duplicated streams were redirected to a room on the floor below, where NSA specialists analyzed the entire through the building of information.

The device, officially called Narus STA 641, was installed in the 6400A room. It is a powerful analyzer of Internet traffic that allows you to filter out the necessary information from a huge stream of Internet data and save the result on the server for later analysis and study in the interests of the US government and special services.
The "shop" functioned successfully until 2006, until the former AT&T technician and now a simple American pensioner, Mark Klein, attracted public attention to the problem of illegal wiretapping by the US intelligence services.
M. Klein gave convincing evidence of the existence of the "black room", spoke in detail about the technical features of cyber espionage, made written statements to senators and representatives of news agencies - under intense pressure from the media, AT&T was forced to confess to voluntary and compulsory cooperation with the special services. A universal scandal broke out.
The interests of M. Klein and everyone who was outraged by the actions of the American special services were represented by the Electronic Frontier Foundation (EFF), a non-profit human rights organization whose goal is to protect the rights and freedoms written in the US Constitution in the era of modern high technologies. AT&T was flooded with lawsuits, the reputation of the NSA itself was seriously "tarnished".

At the same time, specialists from AT&T and the NSA, who had a direct relationship with the "room 641A", justify their actions by the fact that in the current era of high technologies and the universal computerization of modern life, it would be too naive to believe that the state will not use these technology to their advantage.
The fight against global terrorism and drug trafficking, the control of international business contracts, the suppression of financial fraud, cyber attacks and other illegal actions on the part of criminals. Simple people in the street have nothing to worry about - no one is watching them on purpose; the system responds only to the keywords: “bribe”, “cocaine”, “rollback”, “weapon" etc.
Room 641A in the AT&T building on Folsom Street has been permanently shut down. However, Mr. Klein himself and his many associates are convinced that such "rooms" still function in the buildings of telecommunications companies in other US cities - in Seattle, Los Angeles, San Diego, as well as abroad, for example, in a large European communication center in Frankfurt am Main.
A couple of words about the NSA
The NSA, the original abbreviation - NSA (National Security Agency), also contains humorous interpretations of “No Such Agency” or “Never Speak Anything”. A large American intelligence service responsible for all types of electronic intelligence and information acquisition by technical means, interception of domestic and foreign telecommunications, cryptography (breaking of secret ciphers) and data protection.
The number of employees (estimated) is about 20 ... 38 thousand people work at headquarters for "paper work", another 100 thousand technical specialists work at military bases, communication hubs and in the territory of US diplomatic missions around the world. In May 2013, the number of employees decreased by one - the slender ranks of NSA specialists were left by Edward Snowden.
The budget of the organization is a state secret. According to some reports, the amount of funding from the NSA exceeds 10 billion dollars, which makes the NSA the most secured intelligence service in the world. It should be noted that the funds invested in the NSA are returned to the budget with double efficiency - the secret service aggressively protects the interests of American business - a case is well known when the NSA broke the 6 billion contract between Airbus and Saudi Arabia by publishing calls and correspondence of top managers of the company with Arab customers in which the size of the bribe was discussed. Another time, the NSA disrupted the signing of a contract between Brazil and the French corporation Thompson - as a result, the tender in the amount of 1,4 billion for the supply of radar went to the American company Raytheon.
How does the internet work?
It is enough to type in a search bar, for example, some Japanese or American site - and the required information will appear on the computer screen in a second.
How does the internet work? How does the data exchange come about? The trivial answer is by wire, from a local provider (as an option, by air, via 3G and Wi-Fi networks) ... But, in this case, the desired data (content) is stored on servers in Japan or in the USA. How do they almost instantly "fly" across the ocean?
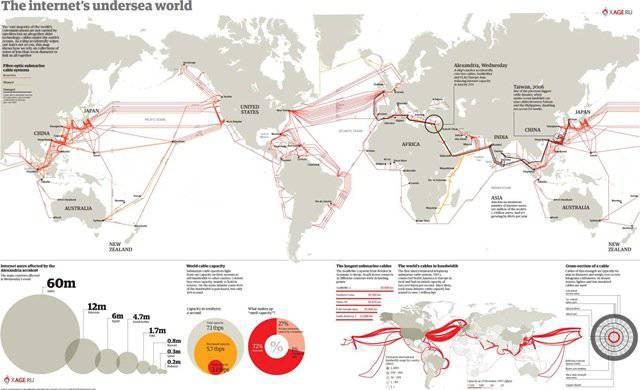
Many are seriously convinced that information is transmitted through telecommunication satellites in geostationary orbit. Alas, this is absolutely not the case - the satellite has a too “narrow” data transmission channel. The capabilities of one satellite was hardly enough to serve a separate provincial town. Satellites are practically unrelated to the Internet - all global Internet traffic goes exclusively through fiber optic cables running across the ocean floor.
This situation provides exceptional opportunities for special services - it is enough to install several devices to intercept data in the key nodes of the circuit and you can be aware of all the events on all continents of the Earth. In this situation, the United States has the most advantageous position - the lion's share of world Internet traffic passes through their territory.

http://www.pbs.org/
http://ttolk.ru/
http://www.wikipedia.org/


Information