How to hack a plane using a smartphone ... And why is it even possible?
Teso is also a professional pilot. So the path to the digital bowels of the aircraft was destined for him. And three years ago, he set out to prove that both little Cessna and a huge Airbus can become a toy in the hands of a trained black hacker. Having sorted through the available options, Hugo settled on three key "pieces of iron" present in many civilian aircraft today. aviation. The first of these is the ADS-B ("automatic dependent surveillance-broadcast" transmitter-receiver).
If in the 20th century, the radar was the main instrument for monitoring the situation in the air of the ocean, today it is being pushed around by “smart” technologies, which allow for more accurate, flexible, and therefore safe escort of aircraft. ADS-B is just one example of such a replacement, which has received international recognition due to its free and open. Basically, this is a very simple thing, based on digital data exchange over the air in the range of about a thousand megahertz. Airplanes that are in the air continuously inform others about their position and course (coordinates are calculated using GPS), and ground services, in turn, collect this information and give back a general summary of the status in the airspace under their control. Since the ADS-B signals are not encrypted, everyone who has the necessary equipment can listen to them. Interesting? Take a look at Flightradar24.comwhere, based on information collected by enthusiast receivers, a global real-time flight chart is compiled.
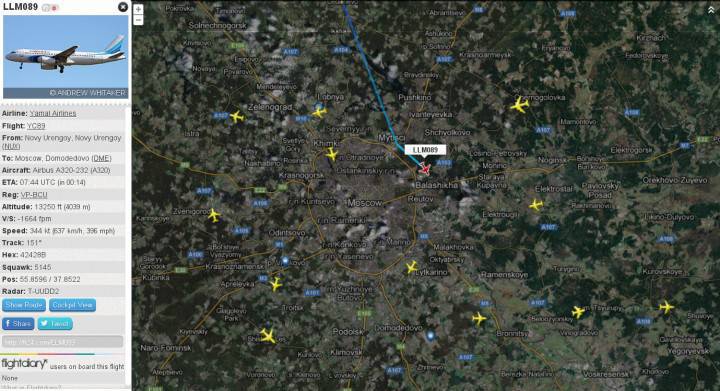
For Teso, groping for vulnerabilities in aviation infrastructure, ADS-B has become the perfect “gunner”. With its help, at any second you can find out exactly where exactly in the three-dimensional space the necessary board is located, where it is going, at what speed, etc. Formally, it may also be a vector to attack, but for this purpose, Teso chose another, more ancient technology - ACARS. If ADS-B is still being introduced (in Europe it is based on 70 percentages of airplanes, in the USA it is still only one in three), then ACARS has been serving civil aviation since the 80s of the last century. This is a slow (2400 baud: as the very first modem) digital communication system that allows airplanes and ground services to exchange short text messages and, more importantly, data packets for the on-board computer (FMS - Flight Management System, on which all control strings are onboard) . As the last Teso chose the popular model from Honeywell.
In order not to put at risk the lives of people, Teso built a digital model of the aircraft at home. Honeywell FMC and ACARS box he purchased on cheap eBay. For visualization, the popular X-Plane air simulator was used. Sending spoof messages was carried out using an SDR device (Software-Defined Radio is a radio station clinging to a computer, the parameters of which can vary in a very wide range thanks to digital control at the deepest level, up to the nuances of the generation and reception process). All this, including the Android-smartphone, on which the attacking application written by Hugo worked, fit into the desktop.
The task posed by Hugo: focusing on the ADS-B readings of the selected aircraft, generate and transmit ACARS packets, the reception of which will lead to dangerous behavior of the FMS and / or inadequate response of the pilots. Theoretically, it only needs to make the onboard computer believe that the forged packages were sent by ground-based air service. And here our hero was waited by the most pleasant surprise: neither ADS-B, nor even ACARS, nor the general architecture of the FMS have any means of protection against forgery. Describing the situation with the security of these systems, Teso (the big joker) uses the expression “facewall”: security is zero, it simply does not exist. Imagine yourself - with today's knowledge - trapped in 80-ies: Internet hardware is designed only with a view to performance, no one thinks about security. Here in this raspberry was Teso. ADS-B, ACARS, FMS do not imply any checks on who sent this or that message, and therefore are subject to every imaginable attack, ranging from banal eavesdropping and ending with DDoS and spoofing.
What can be done with an airplane in this way? After feeding incorrect data to the on-board computer, you can make it change course, change altitude, send to collide with another board, start blinking with external lights, throw away air masks - and much, much more. Some actions will be performed by the autopilot, some - by the intervened captain who is guided by erroneous indications of indicators, some will be forced to do the on-board computer itself, in the software of which Teso has found vulnerabilities. Any unauthorized, unexpected action, when there are hundreds of people on board, becomes potentially catastrophic. At the conference, Teso demonstrated some attacks live, on his desktop complex. But he didn’t disclose the most valuable details, in particular regarding the “holes” he found in the aircraft carrier: according to him, after a minor modification, the application he wrote can be applied in reality, against real planes, and therefore he was the first to inform the manufacturers of aviation equipment and aviaregulators Europe and the United States.
I must say, experts (including the US Federal Aviation Administration and the European Aviation Safety Agency) were quick to dispel fears. According to their representatives, the “real, certified hardware” tricks of Hugo Teso will not work. In contrast to the simulator assembled on the table, where the devices, software and protocols are real, but there is no auxiliary attachment, in airplanes security is ensured by a high level of functional redundancy and protective add-ons (roughly speaking, switches that will not allow the liner to corkscrew by forged ACARS -package). Nevertheless, in private conversations with Teso themselves, they (as well as the manufacturers) showed great interest and even offered assistance in further research. And Teso's colleagues (he works for the German N.Runs AG) confirm his words that the attack scheme needs only a little change in order for it to work “in the air”.

However, let us give experts to judge the real danger of loopholes discovered by Teso. Two more general conclusions that can be drawn from this story are more important to us. First, about the weak or absent security of “non-IT” IT systems. Unlike the world of personal computers, where competition is fierce and rapid progress, closed digital systems from the general public evolve according to their unhurried laws. Here they proceed from the assumption that only professionals should use the product, who, naturally, will not use them to the detriment. Therefore, there are “holes” in them that no one is looking for (Hugo Teso found several of these in a specific FMS implementation) and the lack of input checks (ADS-B, ACARS do not have mechanisms for checking the origin of received packets). It is natural to assume that this rule is true for all - let's call them communal - IT systems that serve the average person, but not available to the average person directly.
And the second observation is connected with availability: the degree of involvement of communal IT systems in global communications is constantly growing. ACARS is still able to work independently, but to use the full potential of ADS-B, GPS is already needed and coordination with other participants via the Network is useful. And the same is true of any other utility systems. Take a look at Shodanhq.com. This is a specialized search engine that indexes all sorts of assistive devices connected to the Internet. There you can find ordinary webcams, routers, printers, but also hundreds of millions of more exotic hardware such as traffic lights, components of smart homes, climate systems, scientific equipment, amusement parks, gas stations, etc. etc. (By the way, a quick search for the word “ADS-B” produces several thousand results). Many of them - quite expectedly - do not require a password or use the default one: the owners obviously did not assume that access might be necessary for someone other than themselves.
And now mentally combine all this and agree that the picture emerges at least unpleasant. So far, terrorists are bombing. But today they can use communal systems serving us against society. How exactly, I do not know, in each case will have to include fantasy. The question is whether we should wait for someone like Hugo Teso, but driven by other considerations, to direct the imagination through this course.
Information