Internet control - humanity is trapped
Until recently, it was believed that the "World Wide Web" is a global thing, unique and not controlled by anyone. It seems that the providers do not belong to any single corporation or organization, therefore it is impossible to establish control over them. But in reality it is not. Despite the fact that the Internet allows people from all over the world to communicate with each other, we should not forget that the network was developed by the American military, who are very interested in the question of what people do on the Internet, who they are looking for, with whom they communicate, what they write about . However, all these issues are of great interest to many governments.
To establish control over human life, there are many ways. Many of them are connected with the use of Internet technologies.
For example, today, probably, there is no person who would not know why barcodes exist on packages. This set of strips and numbers makes it possible to control prices and the quantity of goods received, how many goods are purchased, and how many are left. When buying, a stroke is scanned, the cost of the goods is fixed, and new data is entered into the electronic consignment note. If necessary, all this information can very quickly be online. According to experts who are engaged in exposing conspiracies, barcodes do not carry a real threat, because it is too primitive. But some of them, on the contrary, are of the opinion that the use of bar codes is the first step towards mass monitoring of everything that exists. In developed countries, bar codes are used by postal services that can track mail via satellites. Purchased goods are controlled from the point of purchase to the owner’s house.
Even more information comes through credit cards, with which you can determine what, where, when and in what quantity a particular person bought, what services he pays for. And on that day, when cash disappears from circulation, credit cards can become a valuable source of information not only about a person’s acquisitions, but also his life as a whole. So, now the banking service, which is carried out via the Internet, is getting more and more developed, thus, the personal data of a person, and with them fingerprints, DNA samples, letters - all this is collected, transmitted and stored around the world in databases.
Another way to control is chips that are implanted under the skin. And this is not a fairy tale, they can become a reality in the near future. Thus, in particular, VeriChip Corporation has already launched the production of subcutaneous chips. And the president of this company offered George W. Bush, who at that time served as the president of the United States, to chip all immigrants, so that they could be easily found if necessary. Moreover, the company is actively offering its products to hospitals, and in 2004, the use of chips for medical purposes was also approved in the United States. Moreover, in the West at the moment, chips are introduced to a large number of children of the elite segments of society, military personnel, people suffering from dangerous diseases, as well as criminals. Currently, not only in America, but also in Europe, the idea of introducing chips under the skin of people is advertised and lobbied by all available means.
The only structures that support the chipization of the population without any reservations are the security services. Moreover, a method of forcibly implanting chips has already been invented - with a sniper rifle. A new technology from Denmark was invented by Empire North, and the invention itself was called ID Sniper. The system includes a microchip, a software package, and the rifle itself. Immediately after the chip was implanted, a photo of a person is taken with a video camera mounted on a rifle for further study. After that, this person can be monitored via satellite.
In addition, a major role in establishing total control has been played by the information revolution, which began in the middle of the last century. This has led to the interest of the intelligence services of various countries to a variety of digital gadgets. The first to translate this interest into reality were the Americans in cooperation with the British. In 1947, between the leaders of the two countries, an agreement was signed on cooperation in the field of electronic espionage, that is, all the data that one party received was transferred to the other. But later, the volume of information increased so much that it became increasingly difficult to intercept and process it. Especially since the interests of the Soviet Union, the most likely adversary, extended to virtually the whole world. Under the control of the UK was only Western Europe. The Americans controlled only small regions in which their own military bases were deployed. Therefore, it became necessary to attract new partners. But, despite very good relations with the member countries of the NATO military bloc, none of them were invited to cooperate. Therefore, Australia, Canada and New Zealand were attracted. However, information processing was still done exclusively by experts from the United States and Britain.
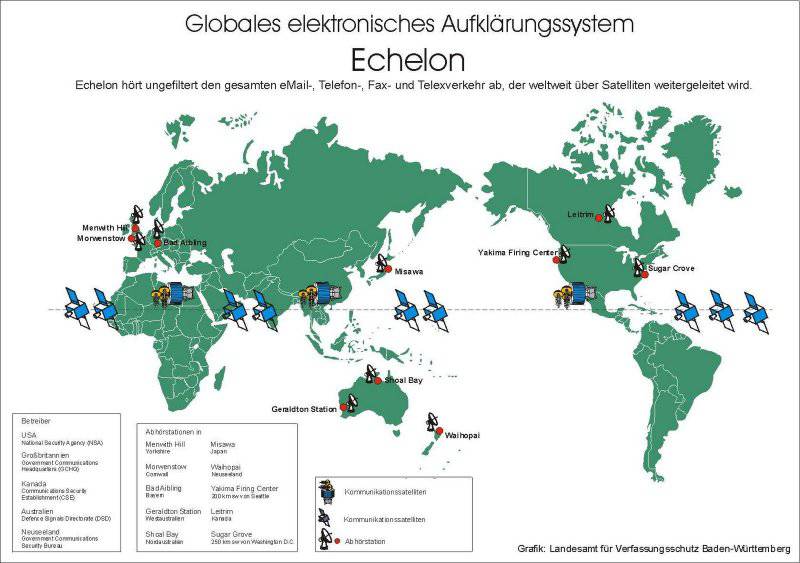
In 1971, a project of an electronic global interception system was developed, called the P-415. The author of the development was the National Security Agency. Thus, enormous opportunities were obtained for intercepting and processing data anywhere in the world. Spy satellites were launched into orbit. In addition, parabolic antennas were installed in Europe and America, which scanned the air, as well as centers for monitoring networks. All these components were subsequently merged into a single system, which was called "Echelon". Thus, the whole world was divided into sectors, for which branches of the system were responsible. Thus, North Africa, Western Europe, and part of Russia to the Urals is controlled by the British Center. The eastern part of Russia and the American continent are controlled by the US National Security Agency, and the South Asian and Pacific regions are controlled by the special services of New Zealand and Australia.
In addition to these countries, several system stations were installed in Japan and Germany, as well as in Israel. Recently, China is among the Echelon participants, on whose territory two top-secret stations were built to intercept data from the eastern part of Russia. It is noteworthy that the Americans initially auditioned the Chinese, but they did it with the help of another NSA station, which is located in Hong Kong, and which was later transferred to the Chinese.
Due to its technical characteristics, Echelon is able to intercept 99 percent of all information transmitted in the world. It is obvious that it is extremely difficult to cope with such a huge flow of information in operational terms, therefore high-speed computers “Cray” are installed in analytical centers.
It is clear that to finance such a large-scale project to a single state is not possible, therefore, the majority of corporations that participated in the creation of the system had a great benefit from cooperation with the special services. Thus, in particular, US auto companies used secret information about Japanese car manufacturers obtained by the CIA. To provide US energy companies with information on new developments in the energy field, an entire Asia-Pacific conference was overheard, held in 1997 in Seattle.
The Echelon project is linked by some analysts with software development called PROMIS, with which you can monitor and coordinate various information about network systems: locate submarines, make predictions on stock market movements.
If you believe the rumors, the US National Security Agency has already learned how to extract a “voice imprint”, that is, there are voice samples in the computer's memory, which can be easily identified by any voice in the audio stream. Thus, if Echelon registered the voice of a certain person, then it can track the telephone conversations of the person who owns the voice, worldwide.
Currently, the Echelon program includes ships, satellites, reconnaissance aircraft, radars, thousands of agents from America, Great Britain, Canada and New Zealand, who control almost the entire planet. The management of some special services that are included in the system are beginning to gradually recognize that this system does exist. However, all the representatives of the security services justify their actions (surveillance, phone tapping, mail interception) in the fight against terrorism.
As for Russia, the collection of information here is very dense, although it is not advertised. Until 1998, the Internet here was considered one of the most control-free communication channels. It is clear that this could not last long. Therefore, in 1998, the State Communications Committee of Russia began to introduce special equipment designed to establish control over all information transmitted in the network. This system has received the official name SORM, that is, the System of technical means for ensuring the functions of operational search activities. If the equipment is connected to the Internet, this allows you to intercept any mail that is of interest to law enforcement agencies. At the same time, the complex works quite simply: all information that is transmitted on the network is divided and scanned according to certain “key” words. Today, almost all service providers that exist in Russia are connected to the SORM system. At the same time, it should be noted that this system is effective only for internal use. To intercept information that comes from abroad, a different system is used - SOUD, or the Unified Accounting System for the enemy. Formally, the agreement on the creation of this system was signed by the Warsaw Pact member states as early as 1977. Its creation was aimed at ensuring the security of the 1980 Olympics of the year, but it began to work a year earlier, in the 1979 year.
The system combines intelligence assets of not only the Soviet Union, but also Bulgaria, the GDR, Poland, Hungary, Czechoslovakia, Mongolia, Vietnam and Cuba. The system contained constantly updated information about Western politicians, businessmen, military, scientists and journalists. Today, SUDS has been transformed into a Russian intelligence system.
But that's not all. Since 1960, the US military has developed a communication network (in other words, the Internet) that was able to withstand even a nuclear attack. With this network, all military and university sites and computers were combined. In 1981, the network was divided into military and civilian. The military component of the Internet gives occasion to some experts to assert that such search engines known to everyone as Yahoo! and Google is a side effect of the NASA project. According to one of the hypotheses, both of these search engines were developed and created in order to detect potentially dangerous information for America, as well as collect data about people who often use certain keywords and expressions in their queries.
Moreover, the Google search engine has already patented the method of observing online games, with the help of which it draws certain conclusions regarding the desires and motives of the players. Other search engines are also actively cooperating with the special services. At the same time, Google remains one of the most powerful and complete directories for satisfying virtually any human request. In addition, here you can find pictures of any corner of the planet, as well as using the webcam to see those places that are most of all interested.
This search engine is developing very quickly, so it is possible that very soon there will be enough information to fully capture the life of humanity.
It must be said that the use of social networks, which are very popular in the modern world, also pose a great danger to humans. Of course, on the one hand, this is a huge amount of unique content, including preferences, requests and much more. But on the other hand, during registration, the user must enter his personal data: first and last name, date of birth, e-mail address. In this case, all the data provided by some of the social networks, for example, Facebook, can use in their personal interests, and moreover, will not bear any responsibility for this.
If we talk about the present, then it should be noted that the establishment of total control over people is gaining momentum. So, in particular, in the United States of America this year the amendment to the law was extended, which makes it possible to intercept e-mail and dry up telephone conversations of American residents without judicial warrants if there is a danger of a terrorist attack.
In addition, the FBI created a new division, the National Domestic Comminications Assistance Center, whose main task was the development of new surveillance technologies, which include spying through the world wide web, intercepting electronic messages and wireless communications (including Skype).
As for the service called Skype, the company Microsoft, which owns it, agreed to listen to the secret services and read the correspondence of users. A similar situation can be traced, for example, in Ukraine. For a long time, the service was a serious barrier for law enforcement agencies during surveillance, because they used ciphers that reliably protect information from hacking. Now law enforcement agencies, according to the privacy policy of the service, can receive personal data of users, the contents of the correspondence in the case of a legal request. In addition, it must be recalled that last year Microsoft had patented a program of “legal intervention”, which allows the judiciary and law enforcement agencies to intercept information without the knowledge of the owners, to eavesdrop on their conversations ...
Thus, it seems that humanity is in a network cell, from which it is almost impossible to get out. And this is not about persecution mania, although it may well evolve from all of the above. Just somehow you do not feel very comfortable when you know that every step you take, every action is controlled and can be used against you ...
Materials used:
http://x-files.org.ua/articles.php?article_id=2805
http://ru.wikipedia.org/wiki/%D1%CE%D0%CC
http://www.rewer.ru/Snoski/Statii/sorm.htm
http://www.cyberpol.ru/sorm.shtml#p_02
http://forum.bakililar.az/index.php?showtopic=80451
Information