Operation "Ultra", or the Story of how the Poles with the British "Enigma" hacked. 2 part

Hans-Tilo Schmidt. Source: wikipedia.ru
However, until the arrest, the traitor to the ideals of the Third Reich actively collaborated with the French and, in particular, handed them 38 code books for Enigma. And if the Germans did not occupy France and did not find evidence of the presence of a mole in the archives of enemy intelligence, then Schmidt would have remained undetected. Polish cryptanalyst Marian Rezhevsky spoke very eloquently about the importance of the agent: "Ashe's documents were like manna from heaven, and all the doors immediately opened." But back in 1931 year, where representatives of the Second Bureau (French Intelligence) agent Rudolf Lemoine and the head of the cryptographic department Gustave Bertrand hit Shmidt on the hands, and the deal on 10 thousand marks took place.

Rudolph Lemoine. Source: wikipedia.ru
French cryptographers got acquainted with the most valuable information on the Enigme machine, understood how it encrypts messages, but could not decode its messages on its own. The upset specialists of the Second Bureau turned to the British, but they too were powerless. Having received the relevant powers, Gustave Bertrand handed over information to Polish cryptographers, but they only concluded that the Germans had adapted the commercial Enigma for army needs. Even European cryptographic leaders, the Poles, could not provide any special breakthroughs in decoding. As a result, the agents of the Second Bureau began to sway the old acquaintance Hans-Tilo Schmidt, who, obviously, had already spent the fee for the deal. As a result, in May and September 1932, Schmidt handed over to France new key installations on the Enigme.
The contacts of the Poles and the French in the decryption sphere were very peculiar: the specialists from the Second Bureau could not independently figure out the codes and bowed to the Poles. And the representatives of Poland willingly used the intelligence of a foreign country and in every way assured the French that the matter would be resolved soon. In fact, Poland was very reluctant to share the results of work in the direction of "Enigma". For the allies, it remained a secret that in this country a model of a German encryption machine was already built for a full-fledged break-in of decryption techniques. Moreover, by the year 1933 the Poles could actually read the Enigma encryption. And here again, not without the work of intelligence.
In the 1930 years, Polish intelligence services discovered a plant for the production of German cryptographic machines in southeastern Germany. A group of underground workers from 1933, the year was actively involved in the process of studying this secret plant and the results were very valuable for cryptanalysis. But all of this collapsed with the advent of 1938, when the Germans changed the procedure for using key installations, introducing, in particular, one-time key settings that form unique initial positions of the disks, changing during each communication session. From this year on, the Poles had noticeable difficulties in deciphering.
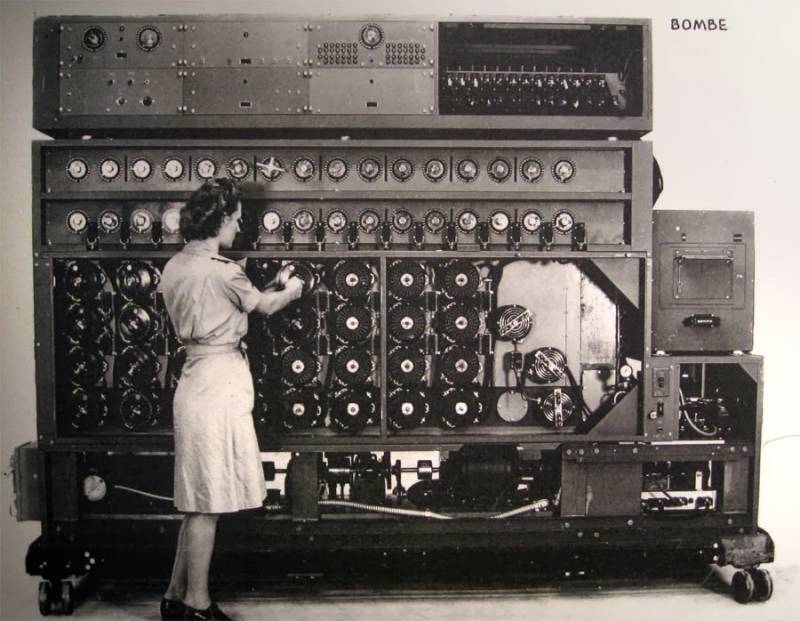
The problem had to be solved somehow, and Marian Rezhevsky came to AVA with a firm intention to make an “Anti-Enigma” capable of “hacking” the German super-cipher. The device was named "Bomb" and consisted of six interconnected "Enigm". The principle was in general terms simple: the message was decrypted by iterating over the initial positions of the disks.
Anglo-Polish model of the machine "Bomb". Source: fofoi.ru
The “Bomb” did this approximately in two hours, while emitting the sound of ticking clocks, for which it received its name. In order to speed up the decryption, the Poles launched several Bombs in parallel. It is noteworthy that the whole story was out of the knowledge of the British and French, who continued to share with Poland the results of the intelligence work with Schmidt. Difficulties "Bomb" Germans delivered in 1938 year, installing five disks at once, of which only three participated in the key installation. The Poles were crazy about breaking such material, and in the summer of 1939, they turned to the British and French for help. Two days in July of the same year in Warsaw, English cryptanalyst Dilly Knox, director of the English Governmental cryptographic school Alistair Deniston, head of the cipher section of the Second Bureau, Gustave Bertrand and his colleague Henry Brackeni came to their senses from the Polish egoism in the “Enigma” question.
"Bombs" at the museum in Bletchley Park. Source: fofoi.ru
In those days, the Poles transmitted one copy of the coders of England and France, as well as a genuine innovation of those times - punched cards with detailed instructions on how to use and make them. When the Germans occupied Poland, the local cipher bureau fled to France through Romania, destroying all Enigma and Bombs in advance. They did it masterfully, the Nazis did not even suspect the very fact of Polish work on decryption. From that moment, a joint Franco-Polish work began on the problems of German codes - until April 1940 managed to read 15 thousand orders, directives and other enemy messages. When it was France’s turn to become part of the Third Reich, the work naturally had to be curtailed, but it did not succeed so carefully, in Polish, to remove all traces, which allowed the Gestapo to finally follow Hans-Tilo Schmidt’s trail.
The British inherited the Polish legacy best of all by organizing a large-scale operation “Ultra” on their territory, gathering their best linguists, cryptographers and mathematicians in Bletchley Park in the county of Buckinghamshire. The distinctive side of "Ultra" has become a unique mode of secrecy, which the British surrounded Bletchley Park. The former head of the UK security service, F. Winterbotham, once said: “I indicated that very strict rules will be required to regulate the number of people who may know about the existence of such information, and special rules for those who receive information: the prohibition to take Any actions that may cause suspicion of the enemy, or confirm his fears that the Allied Command knew his plans ... In certain circumstances, it may be tempting to strike that blow ast secret ... "And the British have made great strides in the implementation of their" ultra-secrecy. "




Information